IOT SECURITY FROM EDGE TO CLOUD
Best practices to enable ioT applications that are trusted and secured from end to end

Best practices to enable ioT applications that are trusted and secured from end to end
The IoT ecosystem is composed of many standards, vendors using different hardware, software and third-party services and APIs. This huge fragmentation makes the ecosystem very vulnerable to all sorts of attacks, both at the edge and in the cloud. This is why it is important to consider edge to cloud security.
To achieve IoT security, we need to establish solid solutions for device discovery with secure identity, authentication and encrypted communications or the underline protocols are subject to abuse.
The IoT ecosystem is composed of many standards, vendors using different hardware, software and third-party services and APIs. This huge fragmentation makes the ecosystem very vulnerable to all sorts of attacks, both at the Edge and in the Cloud.
Often companies make important mistakes when planning IoT solutions, for example:
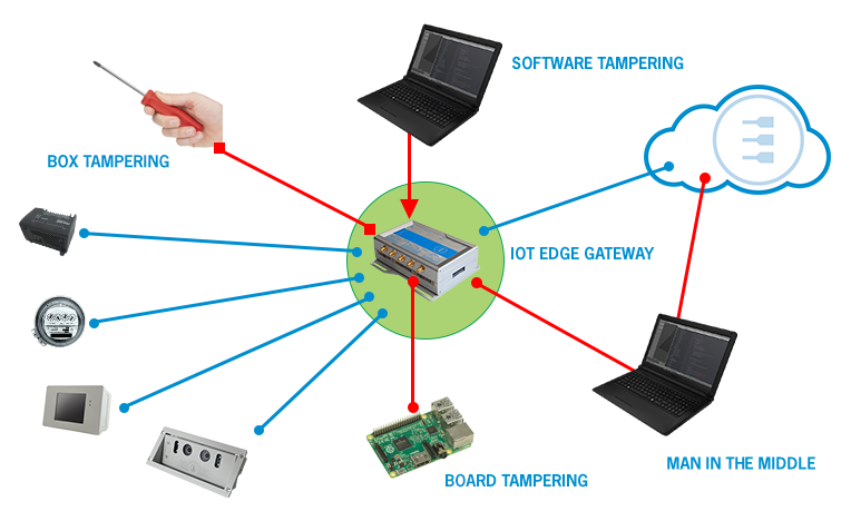
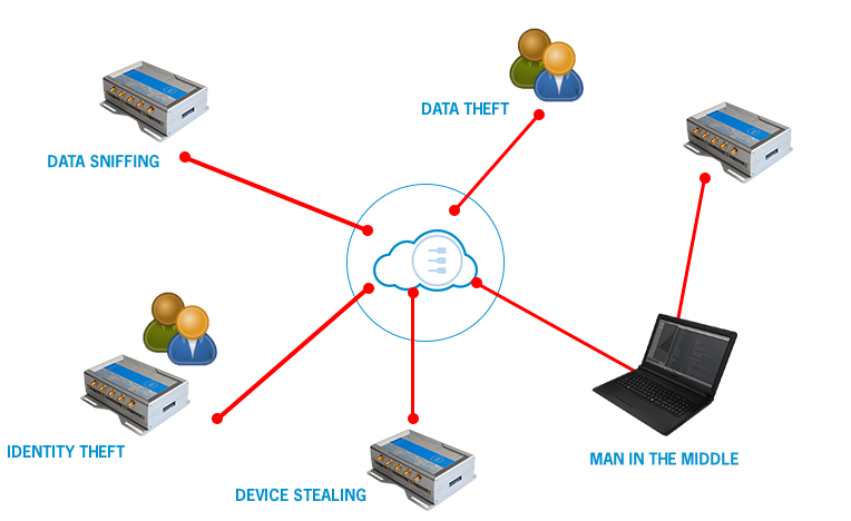
To achieve IoT security, we need to establish solid solutions for device discovery with secure identity, authentication and encrypted communications or the underline protocols are subject to abuse.
Best practices need to consider the specific aspects of distributed mobile systems and devices. We need a secure execution environment for all devices and the IoT integration platform, as well as secure software management distribution. Above all, connected devices and the IoT platform must have a validated identity. To achieve this, we must:
As described before, IoT security must be designed from day one. The illustration below shows how the architecture of an IoT Solution can be divided into three layers:
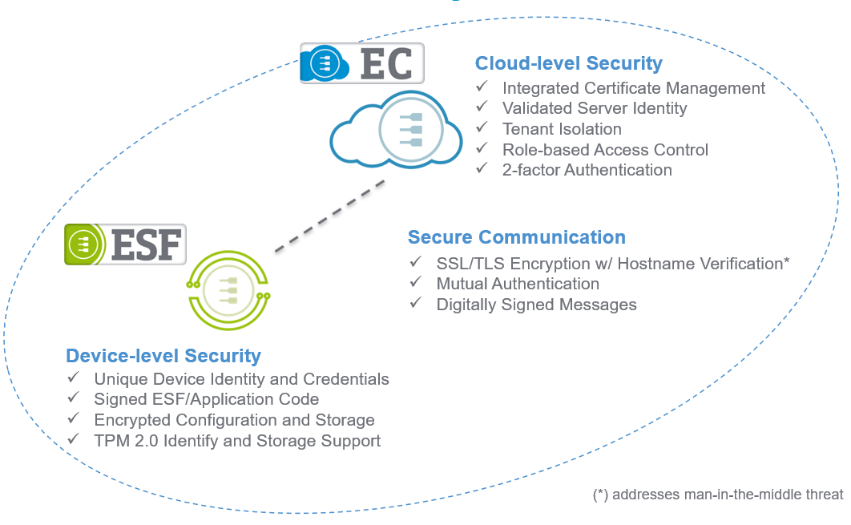
Security mechanisms are an integral component of the Everyware Software Framework (ESF), which in turn is embedded in the IoT Gateway.
The ESF architecture is based on different software layers. The OSGi (Open Services Gateway Initiative) layer provides a good foundation for securely managing software components (signed bundles). ESF ensures that strict Java and OSGi security policies are enforced at runtime and verifies that only software signed by the approved authorities is installed and enabled.
The ESF Security layer encapsulates all the security features and it is supplemented by other measures like secure boot, appropriate hardware design and other measures, thereby ensuring proper protection of the solution on the Edge.
An operation overview of the ESF security can be found here.
Moreover, maintains a list of security guidelines to be followed when hardening an IoT device for a production deployment. The guidelines are compiled following the recommendation of Industry Standards such the Center of Internet Security (CIS) and the IEC 62443. The Eurotech hardening guidelines are available here.

Eurotech supports different protocols, but we advocate the use of MQTT (Message Queue Telemetry Transport), which is a lightweight protocol optimized for IoT device communications:
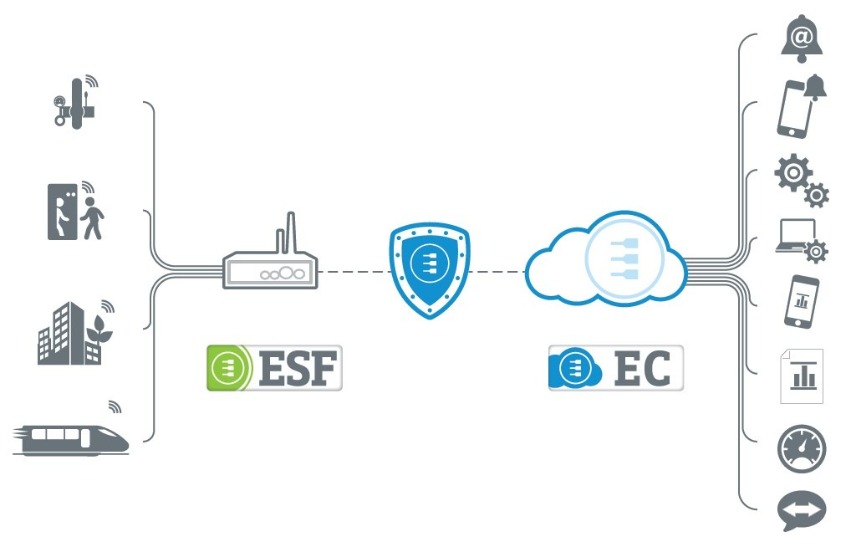
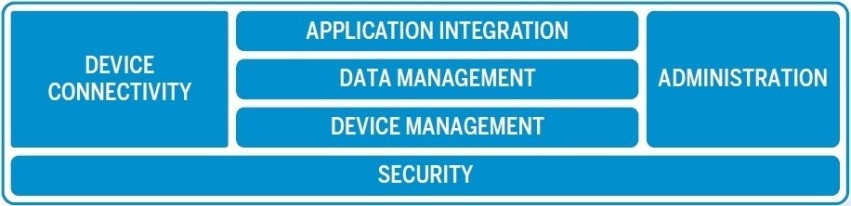
Everyware Cloud unites the operational technology (OT) domain and the information technology (IT) domain, which means that it is the single, most important interface. A success attack would enable access to the enterprise environment. Everyware Cloud also functions as an M2M / IoT integration platform that acts like an operating system for the infrastructure.
On the operational technology side it provides all the data, device and embedded application management required to deploy and maintain distributed intelligent systems in the field. This schematic indicates how security is embedded in Everyware Cloud.
What's the largest roadblock to realizing the promise of the Internet of Things? For many organizations, the obstacle delaying widespread deployments is the strategy for onboarding the necessary edge resources for a lifetime of secure operation. This paper presents the solution offered by Infineon Technologies, GlobalSign, Eurotech and Microsoft to address the complex task of the onboarding of edge devices to the cloud application infrastructure.
DOWNLOAD THE WHITE PAPER